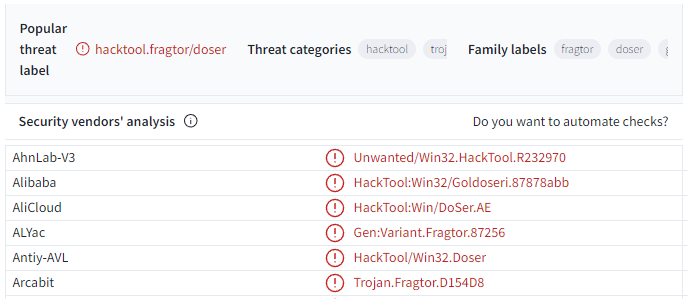
Strange Hacking Tool
Malware sample of unknown category from MalwareBazaar. Just looking to perform a quick analysis and share any interesting findings.
1. Preliminary Analysis
The malware came wrapped in a strange icon: A reverse image search finds its origin from Super Mario Bros’ assets.
![]()
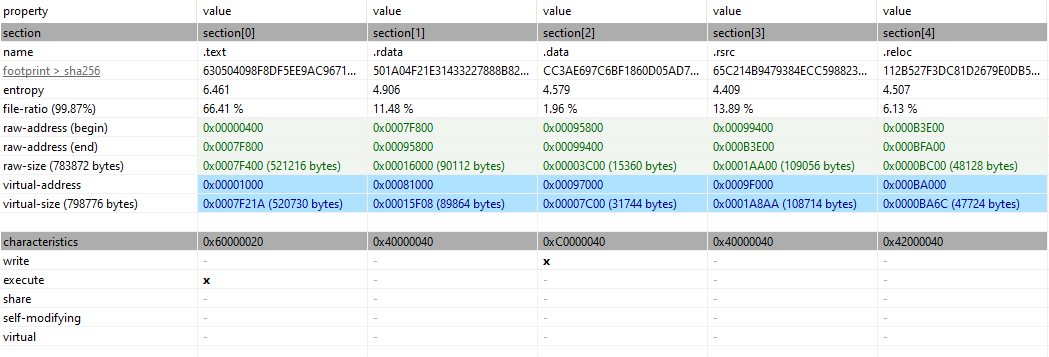
Pretty standard sections and permissions. Nothing unusual here.
The sample does, however, import many suspicious libraries - some of their uses I can only make preliminary assumptions.
- Anti-Debugging -
EnumDisplayMonitors,GetMonitorInfo,EnumResourceLanguages,EnumDisplayDevices,HeapQueryInformation,GetAdaptersInfo - Shellcode/Unpacking -
VirtualProtect,VirtualAlloc - Networking -
WSASocket,WSAloctl,WSASend,WSARecv
Running floss malware.exe returned a whole bunch of garbage strings, indicating that the binary could be packed. Besides that, there were nothing else of interest in the floss output.
...
h8$I
Y_^[
PQQSVW
Y_^[
0SVW
Y_^[
v=h@
h8$I
v=h@
h8$I
v=h@
h8$I
Q`Rj
...2. Detonation
Upon double-clicking the malware, this window appears… 😭😭❓.
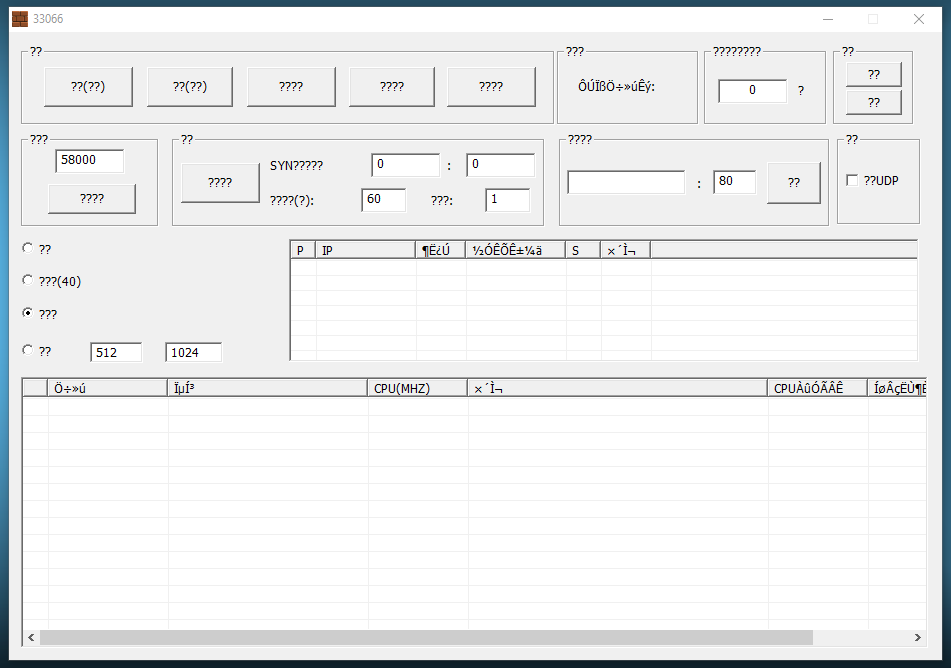
Procmon didn’t observe any abnormal operations. No DNS lookups. No files dropped. If the sample truly is malicious, there must’ve been some anti-analysis checks, or unmet conditions.
But rather, I suspect this might be closer to a ctf challenge, or a hacking tool.
3. Investigation
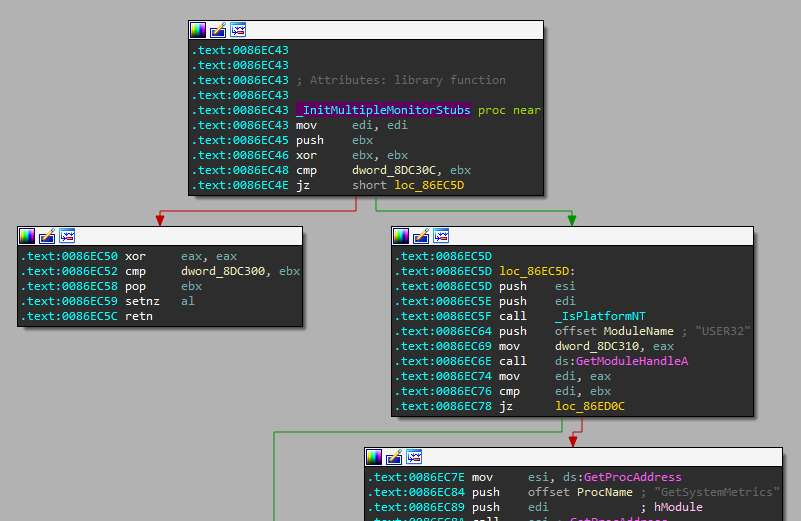
It seems that the abovementioned anomalous WinAPIs EnumDisplayMonitors, GetMonitorInfo, EnumDisplayDevices were just part initializing the window - not for anti-debugging purposes, which I had initially thought.
Attempted to set up a netcat listener with ncat -nvlp 80 to interact with the sample. It failed with an error (god forbid I know). The display window and fields look quite similar other Denial of Service (DoS) tools, such as the Low Orbit Ion Cannon.
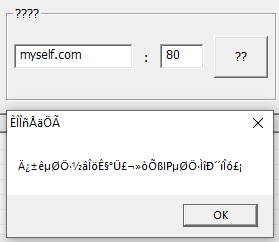
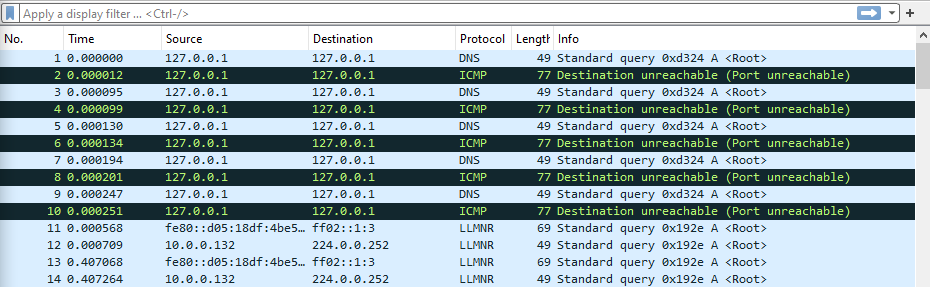
There were some Wireshark DNS and LLMNR logs generated.
4. VirusTotal
Despite multiple attempts to force malicious intent out of the sample, it seems like just a hacking tool.