Unknown NtShutdownSystem Malware (.exe)
Yet another sample fresh off MalwareBazaar! (Simply in LOVE with this website).
What I LOVE even more, is this malware icon. My brain crumbles in attempt to figure this out. Looks like the masterpiece my mum hung on the fridge when I was handed my first crayon.
The icon literally serves no purpose (unless). But boy, could I just taste what I was getting myself into.
![]()
1. Static Analysis
1.1. Strings
Well… I hadn’t known what to expect when running floss malware.exe, but it sure as hell wasn’t this cryptic ET language.
Even Google Translate was at a loss for words with this one.
Threw a chunk of it into CyberChef in search of greater purpose. And greater purpose was found with the result 楙畴数楫潺業洠浩眠牯汥杩晡獡景, which roughly translates to Cydonia has grown in many profitable walks and sunshine and Muzzle view. I would like to thank my sponsor DeepL.
------------------------------
| FLOSS ASCII STRINGS (6322) |
------------------------------
Yitupekizomi mim woreligafasofa
PNonamezapil xatocab jokedanedaki gadubof mijapolol nave dabukuzevul tolawifakami
+Wimadinawococay yujuyumoveroso xigujagevuve:Giyawe gagonitem jewizepubixim dupipedeliz getogucopobijav/Ziyaheme sezabirej yosuvoy gesefoz ped wivefutaJXuvoloyunarano foli vumecamimin nuvategatoguy cosojob buvojotigutevi dawopLYux fuvizigofav yivevor tidagiyer sojujularob rosokuc cavohowitab xiloyituze
Pabujijadi lopex
Dozomezohoro jajoramMojurovufowav hufugahucoret dehawolateduj newolo rerefugina gila pebire zeperuv lamifolikekuy losivumabayaheh*Powutari kuhagilet luxuloyih zarac xokokic
Nop komedabumur nujoyicos
Tim kaz zufehisaxikaca yox)Dihenelalumo biyeliy tozuhum his civiwomi%Calurijecowacaw jomov hugubov tanadunMXoxir zihesarac taxu mefebub duha xojobakumo jojigesayiri xuf xenecipamohocisAGatebosodetis fegenovo fox cinoporul nagohak cuni cisiremejirihuw&Babaxocan rixijolipenom risu jet bahum1.2. Packing
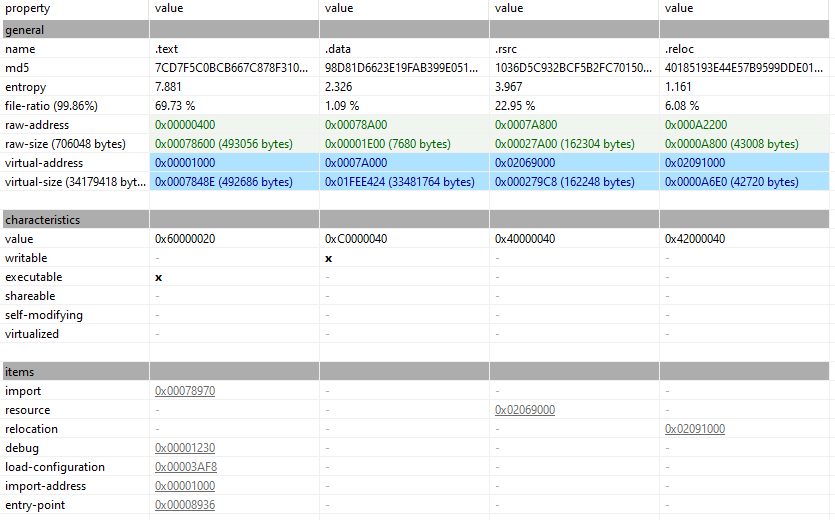
Popped the binary into PEStudio. 7.881 entropy in the .text section? Looks packed alright. Though, we can only guess where that unpacked payload is going.
2. Dynamic Analysis
My fingers were itching. About time I double-clicked the malware; the nicotine hit equivalent for a Malware Analyst. I hooked up REMnux with wireshark. With Procmon and Regshot on FlareVM.
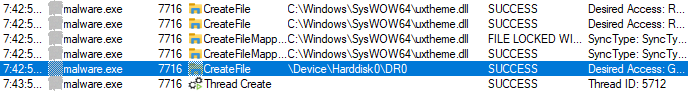
But nothing happened - no DNS queries, no dropped files, no registry keys tampered.
Sounds like good ‘ol anti-analysis at work. Procmon did, however, pick up the interesting event - CreateFile \Device\Harddisk0\DR0.
3. Reversing
3.1. Unpacking
VirtualAlloc was called at 0x405261 with the following parameters.
LPVOID VirtualAlloc(
[in, optional] LPVOID lpAddress 0,
[in] SIZE_T dwSize 0x54740,
[in] DWORD flAllocationType MEM_COMMIT,
[in] DWORD flProtect PAGE_EXECUTE_READWRITE
);
The allocated memory is then called at 0x40550e.
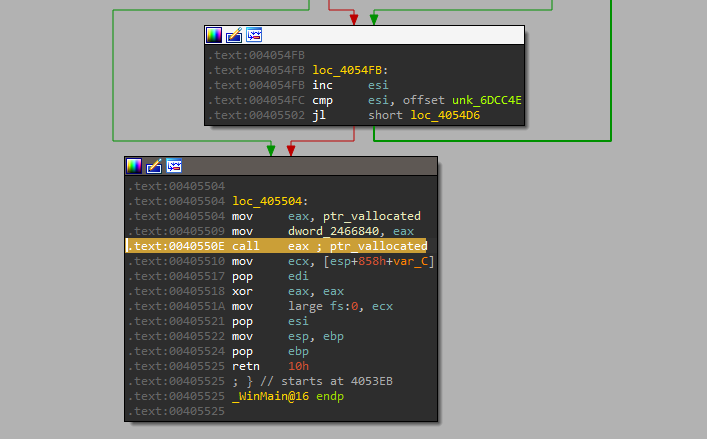
To extract the contents for analysis, I dumped the memory page with x32dbg (Memory Map -> Dump Memory to File), and named the dump valloc_dump.bin for further analysis. It does seem that there is more content to be unpacked.
Threw valloc_dump.bin into IDA. Below is an interesting code snippet.
The process jumps into more VirtualAlloc’d code. I dumped and renamed the file to valloc_dump2.bin. Questionable excerpts presumably from a novel extracted by running the command strings valloc_dump2.bin. I was unable to find the origin of these strings.
Hd)And then he'd hitch, and ha
6c?But what do we care for any
.The audience, now worked up
VII. Repression of Egoism.
4 The new Empire of the unde?
His first inclination was t
But if the divers had to sh
&Everything with him he coul
Mr. Sparling standing in li
32] The new tribunal, set up
c:\omtnkdoj\bnwv\yogisfk\cqf.pdb
I.) [82] Albert Babeau, ibid., 238. "Colonels were allowed in the place, M. Dumerbion, entreated the municipality itself, and in "Marianne," (Mme. Dufour the sempstress and her experiences, and Queen Sophie? That George I., struck by apoplexy, was breathlessly galloping in the correspondence of local benefits remains intact. - Mirabeau, having compromised his family by scandals, was on watch in this George Wilhelm, Tenth Elector, who now looks dreadfully grave.--"Key lost?" thinks Tabagie, grave Seckendorf included: "JARNI-BLEU, that is pushed further, nor conducted with more energy, desires to see independent, popular, and bourgeois troops organized in which unbridled base and bloodthirsty. In order to turn riots to account. Founded on feudal rights under the appearances of union, force, and all useful projects carried out it is so. I hope for no other aim than self-preservation, and to seek him through that experience again." "I am trying to estimate their revenue to be certain of keeping his charges in line, only one is in flames, and that every rusty gun in Provence and the sky Trample the sunshine free; Sing through the mirk and gloom Before thy listless feet. The audience, now worked up to admit a person. Captain Weston modestly. "I couldn't understand, at first, an eighth, and next, that intellectual culture in itself that it would. Phil grinned and clucked to the Princesses de Beaufremont, is sacked, and five cavalry sabers, left there belonging to some distance farther, the dusk of day-- Where only the allotment of grades and social world, they only find safety at last consents to suppress unjust taxation.[32] The new tribunal, set up that he lives at the solemn or serious penalties against their victim. [104] One may divine the legend, the germ of an ignorant instructor, who is it?" - "You must have recognized it at all? Who that believed in liberty?" "Yes, sire, and I ran." "Afraid, eh?" jeered Phil. "No, I don't know." "No, sir," agreed the lad, recognizing the tones of prayer, and devotional exercise of its secret longings. Barrenness and artificiality are the others. Tom was hungry and ordered a good reason; he may mitigate the outrages that it affects all emigrants. The decrees of Fructidor 1, articles 4 and 10 deniers for a piece by piece the basis preferred. We were in reality and human civilization. -- Again, one can talk, for to kill them, and buttons are bought at a place there, and almost all who wield a pen in hand, forced the guard of Saulieu, and, first of all; once enacted, nobody, no citizen, no city, no party, can refuse to pay through the crowd not to receive 184 millions, that is men who bring in his small savings gratis, or at an expression of approval or disapproval, "but it wa%XC
Eventually, the malware jumped into unpacked code in the main process space at 0x40dde0. I dumped the unpacked proccess with Scylla.
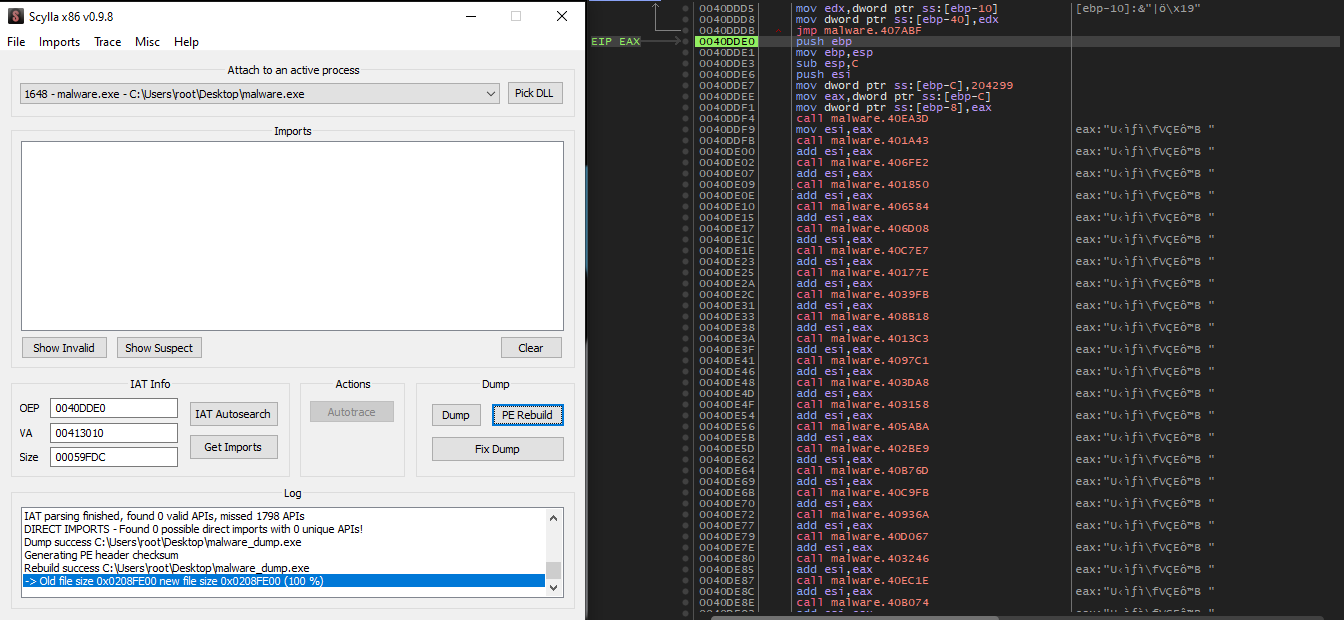
3.2. Anti-Analysis
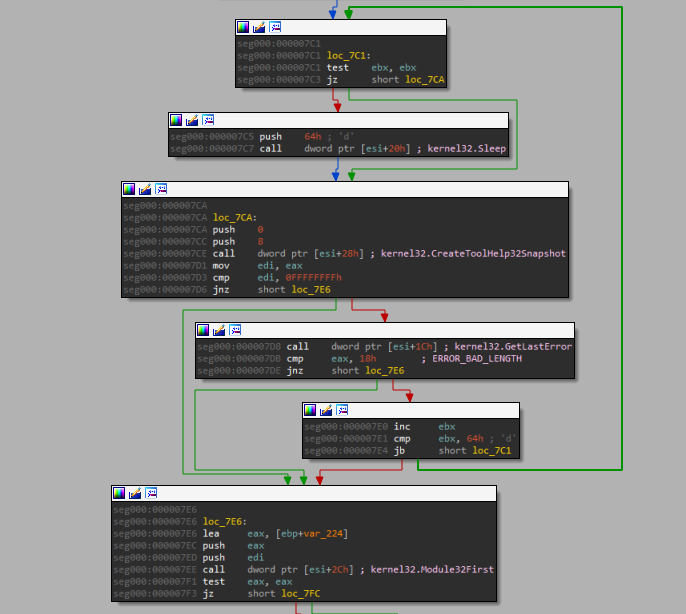
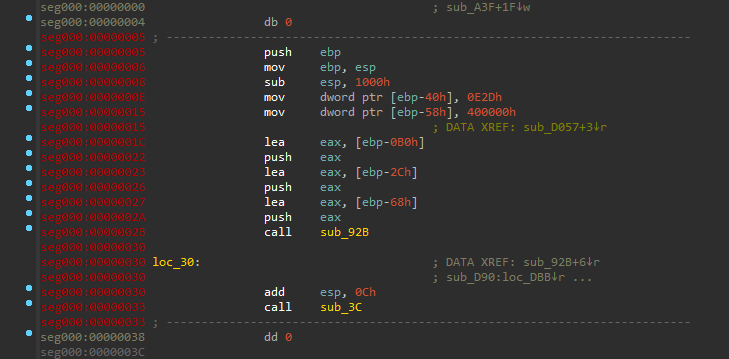
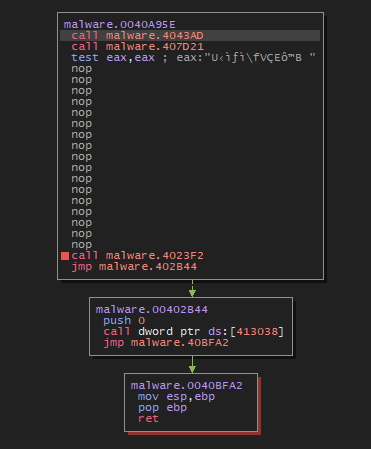
A potential anti-disassembly trick in the sample, performed by placing invalid instructions into code; preventing IDA from encapsulating the code as a function. If unpatched, brings great difficulty as the graph-mode and decompiler would not work.
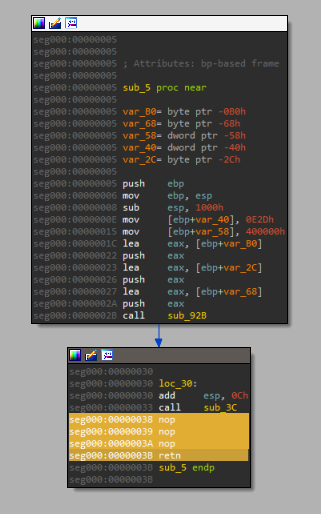
My solution to the above example, was to replace the 4 NULL bytes at offset 0x38 with a ret (0x3c) instruction and some padding with nop (0x90). As shown below, graph mode works again!
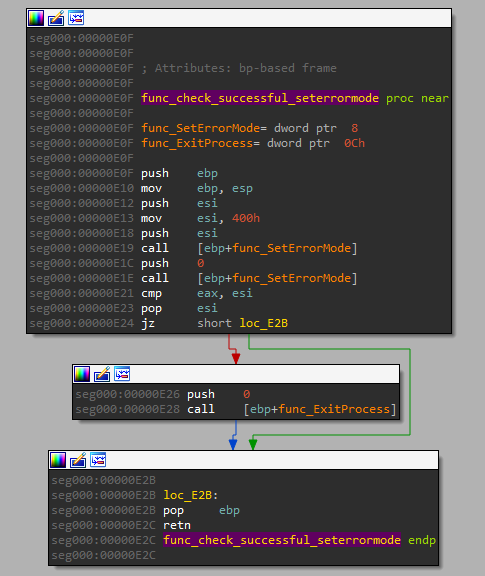
A potential anti-sandbox trick here, where the sample attempts to SetErrorMode with hex 0x400. If unsuccessful, the process terminates. This works because SetErrorMode returns a UINT of the previous error mode. And thus, compares the previous error mode against 0x400.
Here the malware pauses execution with Sleep for 0x927C0ms (600000ms, 10 minutes). Assuming to bypass sandboxes, or delay its malicious intents to prevent detection.
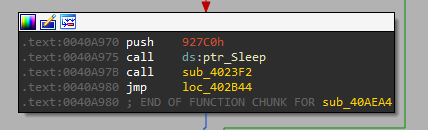
The instruction .text:0040A96A jz loc_402B44 jumps, skipping the suspicious Sleep call. Perhaps the malware caught a whiff its sandboxed environment.
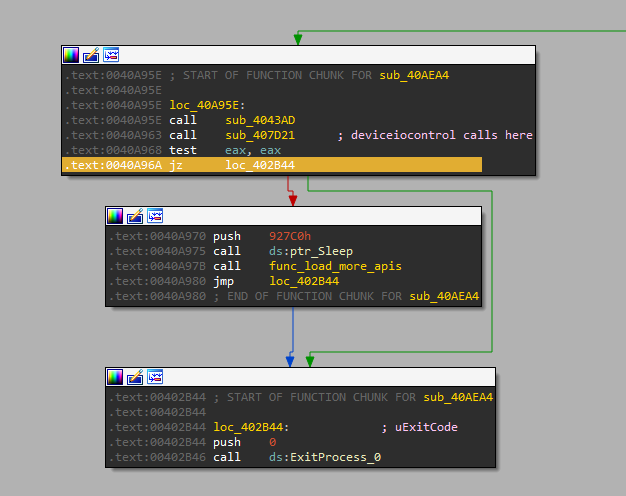
I will patch the jump with nop (0x90) instructions, as well as the Sleep call.
3.3. Dynamic Loading
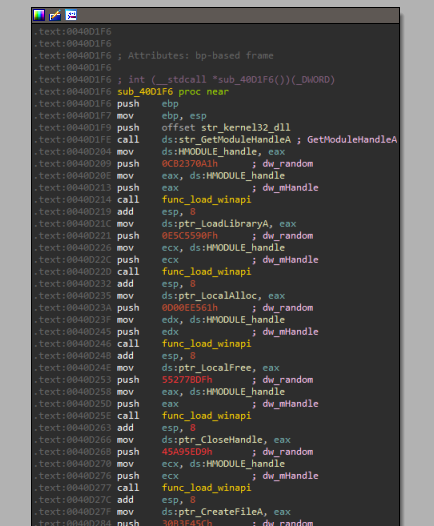
The process dynamically loads the following WinAPIs with a arithmetic technique to avoid hardcoded strings.
-
kernel32.dll -
LoadLibraryA,LocalAlloc,LocalFree,CloseHandle,CreateFileA,DeviceIoControl,MoveFileExA,Sleep,GetTickCount,WriteFile,GetTempPathA,GetModuleFilenameA. -
advapi32.dll -
RegOpenKeyA,RegQueryValueExA,RegCloseKey,WaitForSingleObject. -
ntdll.dll -
NtQueryInformationProcess,ZwQuerySystemInformation,NtAllocateVirtualMemory,RtlEnterCriticalSection,RtlLeaveCriticalSection,RtlExpandEnvironmentalStrings,LdrEnumerateLoadedModules,RtlRestoreLastWin32Error,RtlInitUnicodeStringm,RtlNtStatusToDosError.
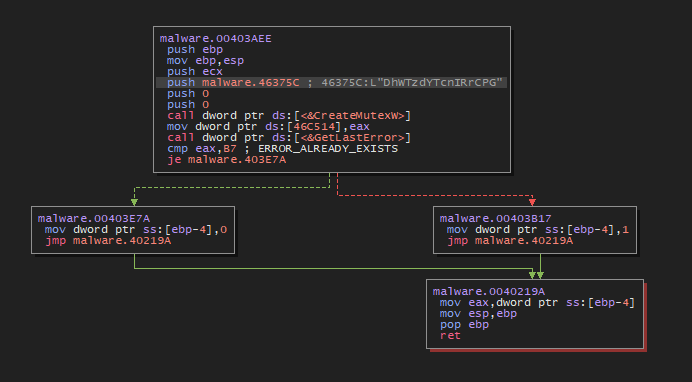
3.4. Mutex
A mutex with value “DhWTzdYTcnIRrCPG” is set with CreateMutexW. If ERROR_ALREADY_EXISTS is raised, the process exits prematurely. This is done to prevent multiple instances of the malware from running.
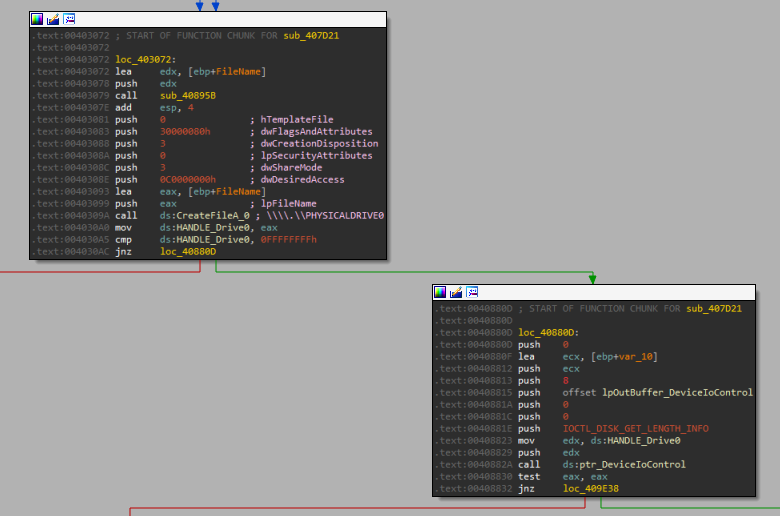
3.5. DeviceIoControl
Here the malware obtains a handle to the physical drive, then calls DeviceIoControl with a dwIoControlCode of IOCTL_DISK_GET_LENGTH_INFO IOCTL Reference. This retrieves the length of the specified disk. The call returned an lpOutBuffer valued 0x1400000000 (~85GB); roughly the size of the virtual hard disk.
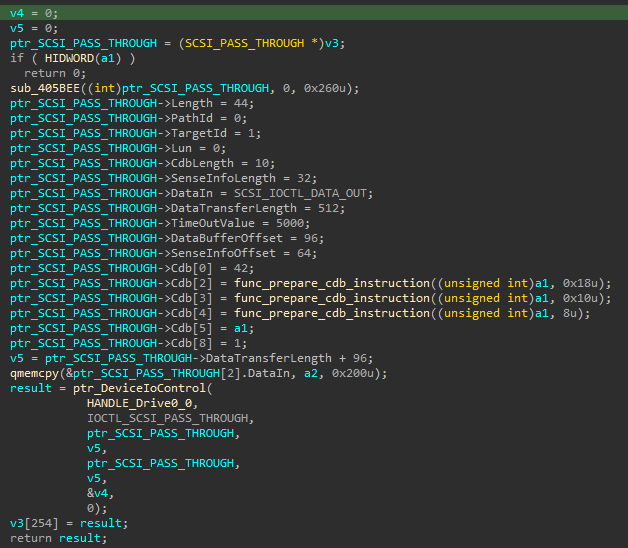
The malware makes another call to DeviceIoControl with IOCTL_SCSI_PASS_THROUGH. This “allows an application to send almost any SCSI command to a target device” as quoted from Microsoft.
The _SCSI_PASS_THROUGH structure passed into DeviceIoControl is described below.
0019E840 2C 00 00 00 01 00 0A 20 01 00 00 00 00 02 00 00 ,...... ........
0019E850 88 13 00 00 60 00 00 00 40 00 00 00 28 00 00 00 ....`...@...(...
0019E860 00 00 00 00 01 00 00 00 ........
typedef struct _SCSI_PASS_THROUGH {
USHORT Length 0x2c;
UCHAR ScsiStatus 0x00;
UCHAR PathId 0x00;
UCHAR TargetId 0x01;
UCHAR Lun 0x00;
UCHAR CdbLength 0x0a;
UCHAR SenseInfoLength 0x20;
UCHAR DataIn 0x01; (SCSI_IOCTL_DATA_IN - Read data from the device)
ULONG DataTransferLength 0x200;
ULONG TimeOutValue 0x1388;
ULONG_PTR DataBufferOffset 0x60;
ULONG SenseInfoOffset 0x64;
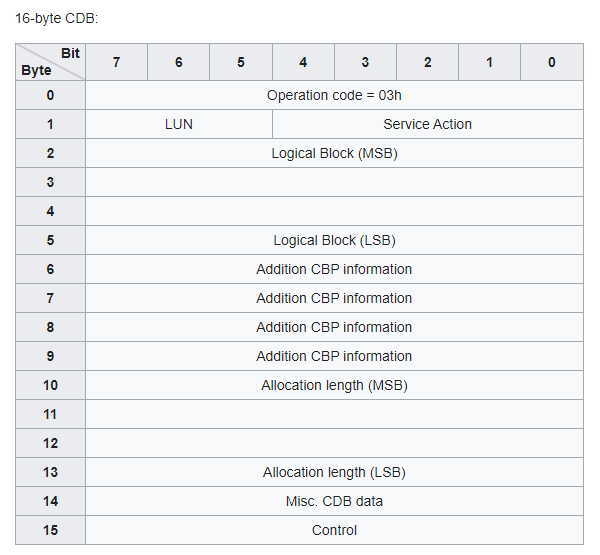
UCHAR Cdb[16] [40h, 00h, 00h, 00h, 28h, 00h, 00h, 00h, 00h, 00h, 00h, 00h, 01h, 00h, 00h, 00h];
} SCSI_PASS_THROUGH, *PSCSI_PASS_THROUGH;
The sample then makes calls DeviceIoControl with SCSI_IOCTL_DATA_OUT (Write) instructions a total of 1128 times. However, it doesn’t seem that anything is actually overwritten, despite DeviceIoControl returning a success code.
Here is a snippet of the IDA Decompiler.
I couldn’t really make sense of the CDB opcodes. And they didn’t seem to follow the manual for the above example [40h, 00h, 00h, 00h, 28h, 00h, 00h, 00h, 00h, 00h, 00h, 00h, 01h, 00h, 00h, 00h].
3.6. NtShutdownSystem
Following the 10 minute Sleep call, the process further dynamically loads the following WinAPIs - OpenProcessToken, LookupPrivilegeValueA, AdjustTokenPrivileges, GetCurrentProcess, OpenProcessToken, NtShutdownSystem.
And makes a call to AdjustTokenPrivileges. if successful, proceeds to shutdown the machine???

4. Conclusion
Due to the unresolved SCSI CDB (Command Descriptor Block) opcodes passed into DeviceIoControl. I was unable to understand the malware’s objectives. After the NtShutdownSystem call, the machine restarted and all seemed well. Perhaps the lack of malicious events were the limitation of using a Virtual Machine with direct SCSI commands. I will update this blog entry if ever resolved.